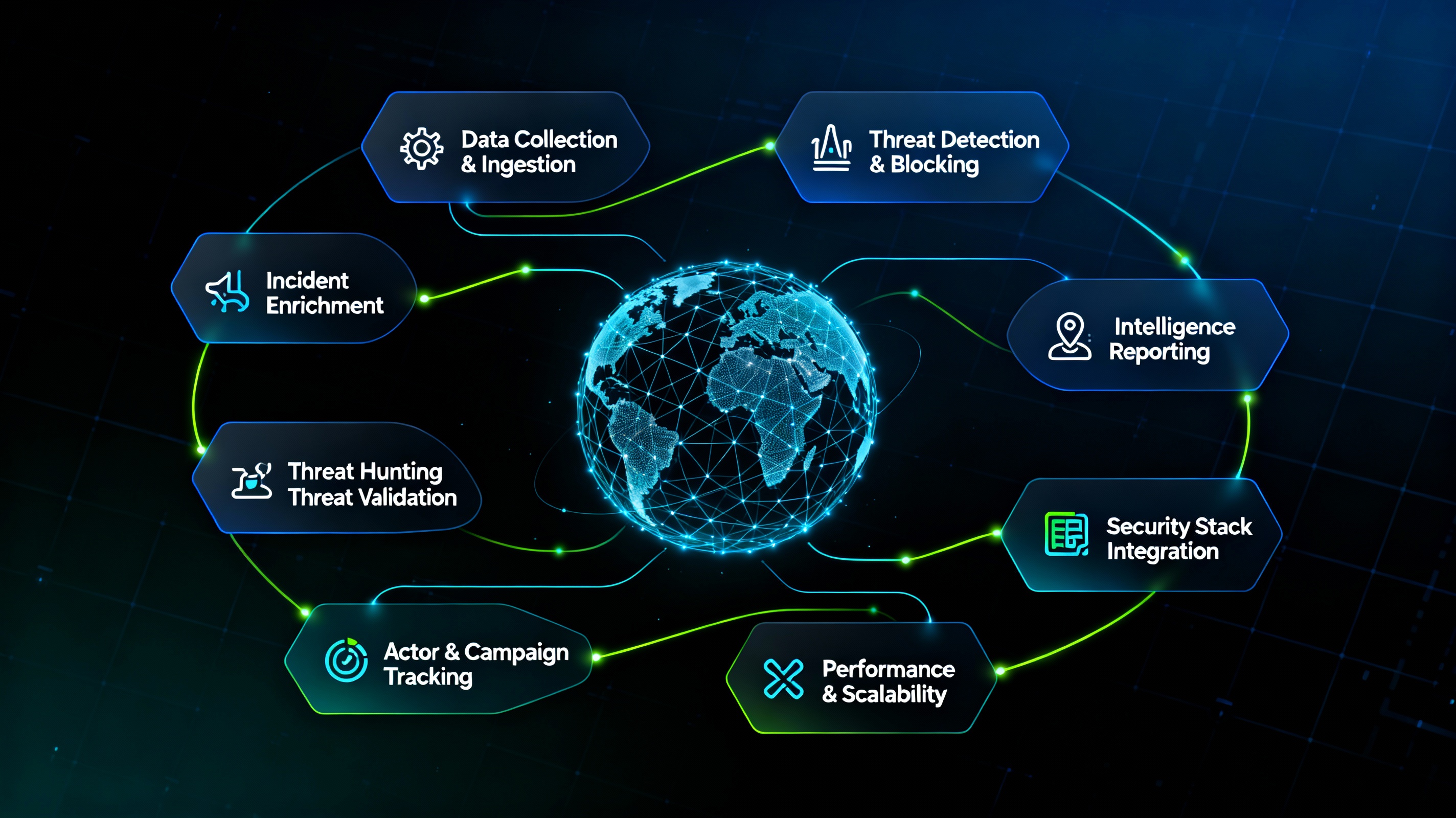
Data Collection and Ingestion
- Verify automated ingestion from multiple threat feeds (commercial, open-source, ISAC/ISAO, dark web, OSINT) with correct normalization and deduplication.
- Test parsing and enrichment of indicators of compromise (IoCs): IPs, domains, file hashes, URLs, and CVEs, ensuring metadata (threat actor, TTP, severity) is accurately attached.
Enterprise: Validate high-volume feed handling (millions of IoCs) with performance and scalability tests.
SMB: Confirm lightweight, curated feed integration without overwhelming small SOC teams or budgets.